Bypassing Laravel Default File Upload Validation
Hello Fellow Hackers, I am Ahmed Kameran , Security Researcher from Kurdistan, Iraq.
Hope you are doing well. I want to talk about one of my research’s in Laravel Core framework which allows to bypass Laravel default upload validation using different PHP extensions.
Laravel Default behavior for file upload restriction
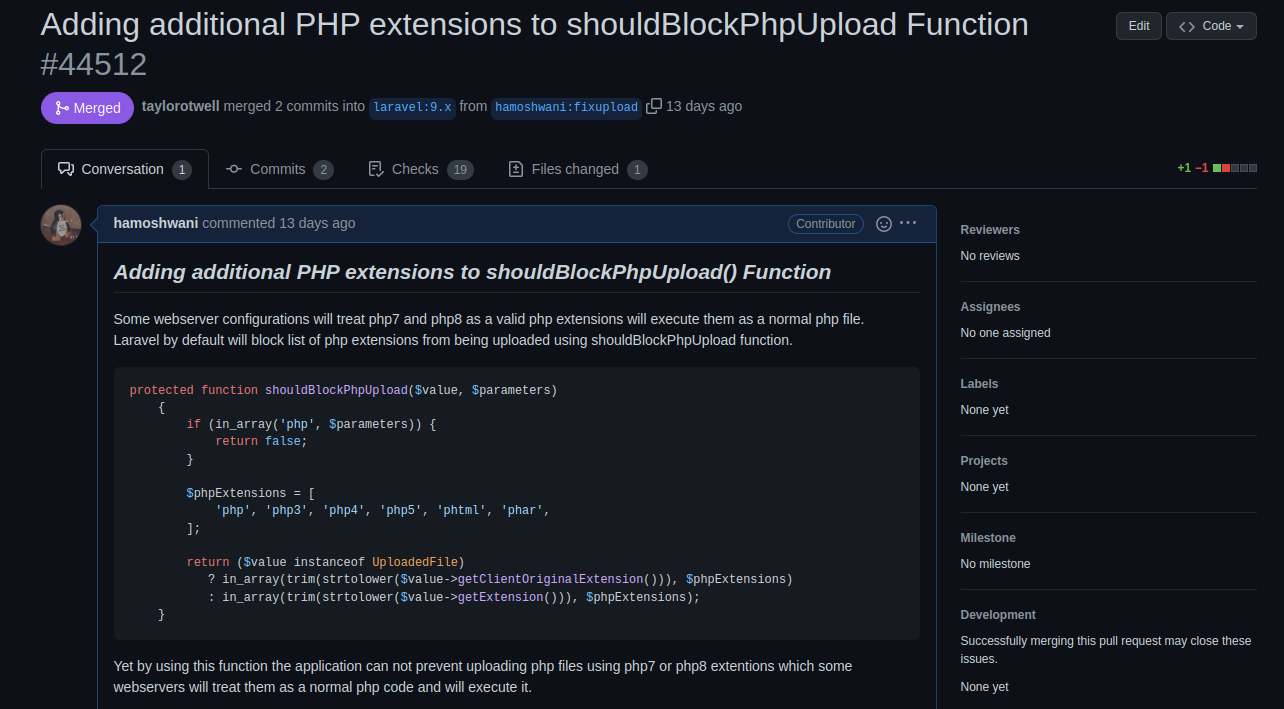
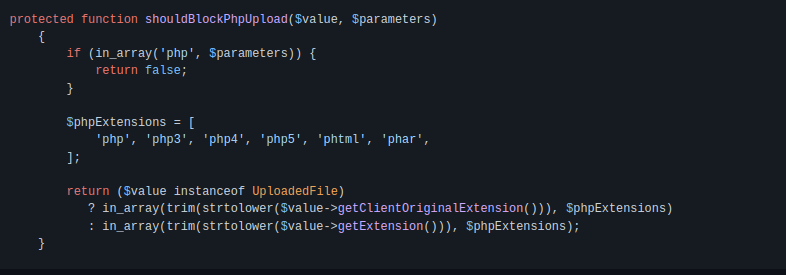
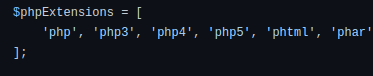
Laravel by default will block set of PHP extensions from uploading into the laravel application using this function.
If you try to upload a file with these blocked extensions the validation will return an exception as these extensions were blocked by Laravel, let’s try to upload a file with (.php) extension:
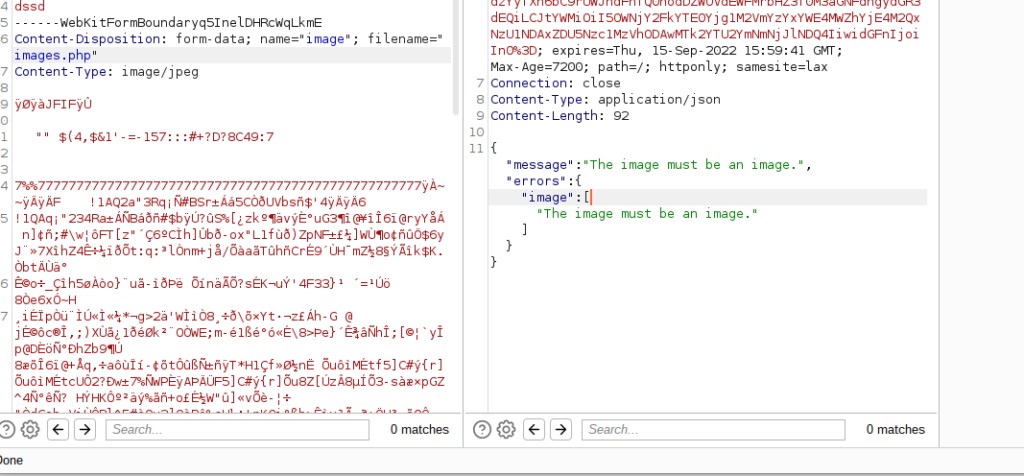
As we can see from above screenshot uploading a file with .php extension was blocked by Laravel file validation because .php was in this array list of blocked extensions:
Bypassing Laravel File Upload Validation
The Laravel default function to prevent uploading .php extensions was not blocking .php7 or .php8 file extensions as some web servers will treat them as a normal php executable file.
Now if we try to upload a file with .php7 extension the uploading will be successful as we can see in below screenshot:
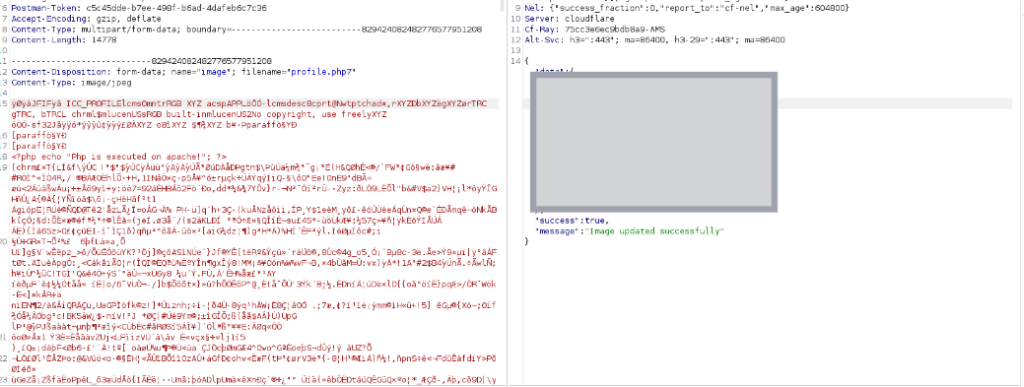
As some web servers will treat .php7 or .php8 file extension as a valid PHP executable like the example below which we uploaded .php7 and it got executed on the Apache web server as a valid PHP which can lead to Remote command execution on any server that accepts php7 or php8 files:

Fixing the issue
I just opened a pull request to Laravel core that i added php7 and php8 into the array of blocked list PHP extensions.
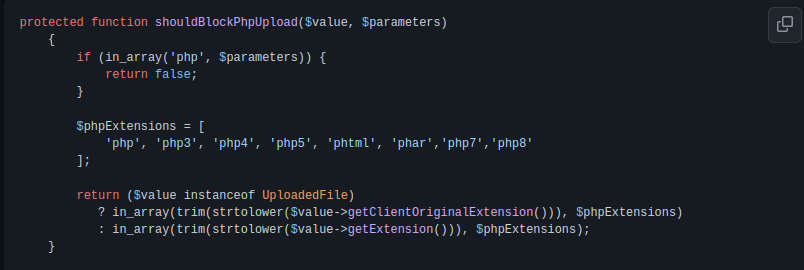
You can find my pull request HERE.
Vulnerable Laravel Applications
This issue was fixed in the Laravel’s latest version (v9.36.1) so all versions before that were vulnerable to this type of attack.
Vulnerable versions
9.x
8.x
7.x
6.x
5.x
Vulnerable Web servers
During my research i found out, A lot of cloud and host providers will configure there web servers to execute php7 and php8 file extensions as a normal php file.
Here is an example of vulnerable configured Apache web server.
This is contents of /etc/apache2/conf/mime.types file
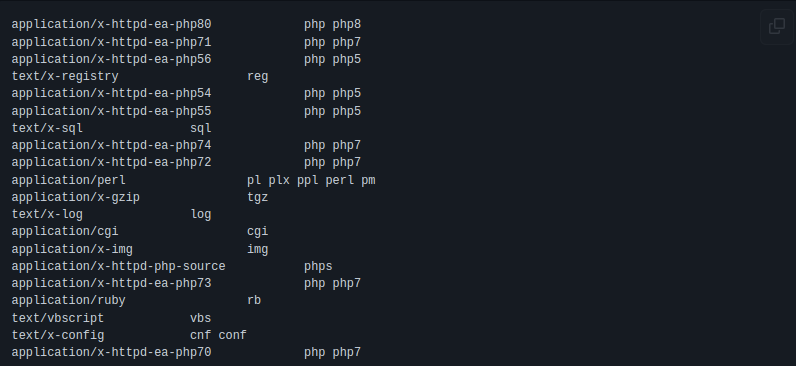
Fixing Web servers
Make sure your web server configuration didn’t treat other php extension types as a valid php file like example above.
Also you can add .htaccess file to uploads directory to prevent execution of PHP in uploads directory which is controlled by end users.
Add this to .htaccess file in uploads directory

Mitigation
Upgrade Laravel to latest version (v9.36.1) or make sure you configure your web server correctly so its does not treat other .php extensions as a normal PHP executable.
Thanks
